|
Wireless Security Guide
 |
Hole 2 -Network Encryption
Whenever you are use a network password, that does not mean that the information will be sent only to those that know the password, nor does it mean that only the person with the password will be able to see the
fact that the information is the there. In fact anyone with the right kind of equipment can intercept this information or know that the information is being transmitted. So how does the password protection work? Well, whenever you create a password, the router and your computer use that password in order to order to encrypt data according to a series of steps that differ depending on the encryption standard you use. There are several standards which you may have heard of, ranging from the WEP to WPA and WPA2.
| Netgear | Linksys |
|---|---|
WEP and WPA in one way or another use an encryption algorithm called RC4 of ARCFOUR. Whenever you enter a password, RC4 develops 2 passwords for you, a public password and secret password using the pass phrase you entered. Whenever you transmit data, the data is encrypted using your private key. Along with that password, an Initialization Value (IV) is passed on. An IV is set of changing numbers that are required to initialize the decryption mechanism in the RC4 cipher. This set of values unlike the rest of the information is sent in clear text thus anyone out there who has the ability of picking up information will be able to catch this set of code.
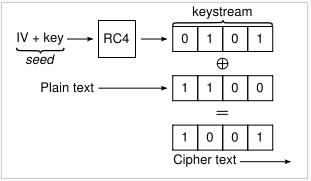
The uses of RC4 differ in encryption mechanisms. The main reason why WEP is not as secure as WPA is because the IV used in the encryption is only 24 bits long, so every 4000 or so packets of information, the same IV number will be repeated. The repetition of an IV is at the very core of the security problem because once these numbers are repeated enough times, the encryption can be cracked. WEP only relies on RC4 for encryption and it is easy to crack (under 3 mins for most cases).
This problem was more or less fixed with the introduction of WPA, or so was thought. WPA increased the IV value to being 48 bits long, which means that a value was to be repeated over a period of years not minutes. In addition to increasing the IV, WPA also uses the MAC address of your computer in combination with a set of randomly generated values to encrypt your data. As a response to this issue other methods are predominant in cracking WPA such as packet injection instead of just packet collection as in WEP's case. WPA's main vulnerability came from its backwards compatibility. WPA implements only some of the IEEE 802.1i security standard since the RC4 is still the cipher that is used to generate keys.

If You Liked this Guide Please Digg
Make your Opinion Count Please Slashdot